SAP & OutSystem Security
How to hack SAP with OutSystems, and how to avoid being hacked.

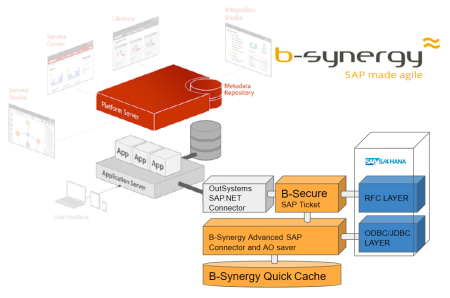
Extend SAP by using OutSystems
A bunch of reasons leads our customers to choose a low-code platform like OutSystems on top of their SAP landscape.
Does this sound too good to be true? Well, it isn’t! But nevertheless, there are some issues that should be carefully considered. One of them is how to deal with SAP’s license model which these pages are about.
Does this sound too good to be true? Well it isn’t! But nevertheless, there are some issues that should be carefully considered. One of them is how to deal with security on SAP-OutSystems integration scenario which these pages are about.
It almost sounds to good to be true, Connect, Search and use SAP Services in OutSystems. Is it really this simple. Off course nothing is ever as simple in the IT world. From a technical perspective usin a BAPI (Business Application Programming Interface is easy enough. But when you do apart from technical and functional SAP knowhow there are some subjects that need thorough observation. One of them being the SAP-OutSystems Security.
SAP, as most OutSystems developers know by now comes packed with functions to create or update their business object like sales orders, purchase orders Plant Maintenance Orders etc. B-Synergy and OutSystems implemented in close collaboration the functionality in OutSystems to consume those functions. Since these functions can be called from outside SAP they are called RFC's (Remote Function Calls). The more complex ones are called BAPI's (Business Application Programming Interface)
Reasons to choose LowCode & SAP
How to hack SAP with OutSystems?
This is a lesson that more and more corporations are learning.
"Although attacks by outside hackers -- people who illegally access electronic systems to obtain secret information or steal money -- generally receive more publicity, insiders pose a far greater threat to computer security," according to The Lipman Report, a monthly management newsletter published by security consulting firm Guardsmark Inc.
OutSystems comes with the functionality to very easily get data out of SAP ECC or S/4HANA by using RFC's.. Most companies that want to benefit from this SAP-OutSystems synergy are not aware and have not implemented Security measures that keep your SAP systems from prying eyes. This comes as a serious security risk and does from a legal perspective could be seen as negligence in court cases where Private data was stolen.
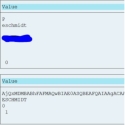
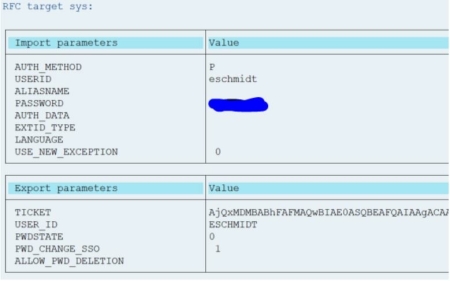
How easy is it actually to breach an SAP System with OutSystems? Well, when you are using a technical SAP user to integrate with OutSystems a junior developer can make ALL of your SAP publicly available for querying.
It is therefore very worrying that all but 1 customer B-Synergy has encountered in almost 10 years of SAP-OutSystems experience has a security layer implemented. Without naming true identities a big dutch brewerie, an orange rental company, a large chemical plant, a large bakery and a major retailer are all at serious risk!
B-Synergy can audit your SAP-OutSystems integration in 1 day to help you avoid intentional or unintentional SAP-OutSystems security breaches. When we find threats you can implement security measures yourselves or implement the security layer as provided by B-Synergy.
When you are an SAP Partner or OutSystems partner, B-Synergy is more than willing to help secure your customers, the employees of your customer and the customers of the customer, another good address company to talk to in this regard is Craig Terblanche- Chief Transformation Advisor at ExoSystems
SAP-OutSystems Security, Better Save than Sorry. ?
SAP-OutSystems Login Ticket
SAP Logon Tickets are native to SAP and will be issued only in exchange for valid credentials (during logon / inbound communication).
-typically transmitted as a (non-persistent) browser cookie
-transmitted whenever the browser sends a HTTP request to a server (domain constraints apply)
-designed to be used for cross-system SSO (Portal scenario)
SAP Logon ticket creation is not supported by OutSystems as a standard function in their SAP utilities
The two ticket-based methods are native to SAP ECC and S/4HANA and are only for native SAP HANA users as it does not map user information into SAP HANA from external applications. Thus, the logon tickets and assertion tickets method is a direct way of user authentication. The users requesting access to SAP ECC or HANA system are issued user-specific tickets using which they get access into the system. The user tickets can be created in the SAP ECC or HANA system or from OutSystems directly through an SAP-OutSystems Security layer as an extension in OutSyst
Difference between BAPI and RFC ?
Business Application Programming Interface
Remote Function Call
All BAPIs are RFCs
Business Object Repository
SAP & OutSystems ODATA
Underwater SAP ODATA services use BAPIs and RFCs for functions that involve business logic. This is because SAP is built on ABAP and conversion must take place from web protocol to sap native ABAP.
SAP & OutSystems SOAP
SAP Business Suite services
OData is a Web protocol for querying and updating data, applying and building on Web technologies such as HTTP, Atom Publishing Protocol (AtomPub), and RSS (Really Simple Syndication) to provide access to information from a variety of applications. It is easy to understand and extensible and provides consumers with a predictable interface for querying a variety of data sources.
AtomPub is the standard for treating groups of similar information snippets as it is simple, extensible, and allows anything textual in its content. However, as so much textual enterprise data is structured, there is also a requirement to express what structure to expect in a certain kind of information snippet. As these snippets can come in large quantities, they must be trimmed down to manageable chunks, sorted according to ad-hoc user preferences, and the result set must be stepped through page by page.
OData provides all of the above as well as additional features, such as feed customization that allows mapping part of the structured content into the standard Atom elements, and the ability to link data entities within an OData service (via "…related…" links) and beyond (via media link entries). This facilitates support of a wide range of clients with different capabilities
Benefits SAP ODATA
More on ODATA
-Human-readable, language-dependent labels for all properties (required for building user interfaces).
-Free-text search, within collections of similar entities, and across collections using OpenSearch. OpenSearch can use the Atom Syndication Format for its search results, so the OData entities that are returned by the search fit in, and OpenSearch can be integrated into AtomPub service documents via links with rel="search", per collection as well as on the top level. The OpenSearch description specifies the URL template to use for searching, and for collections it simply points to the OData entity set, using a custom query option with the name of "search".
-Semantic annotations, which are required for applications running on mobile devices to provide seamless integration into contacts, calendar, and telephony. The client needs to know which OData properties contain a phone number, a part of a name or address, or something related to a calendar event.
Not all entities and entity sets will support the full spectrum of possible interactions defined by the uniform interface, so capability discovery will help clients avoid requests that the server cannot fulfil. The metadata document will tell whether an entity set is searchable, which properties may be used in filter expressions, and which properties of an entity will always be managed by the server.
Most of the applications for "light-weight consumption" follow an interaction pattern called "view-inspect-act", "alert-analyze-act", or "explore & act", meaning that you somehow navigate (or are led) to an entity that interests you, and then you have to choose what to do. The chosen action eventually results in changes to this entity, or entities related to it, but it may be tricky to express it in terms of an Update operation, so the available actions are advertised to the client as special atom links (with an optional embedded simplified "form" in case the action needs parameters) and the action is triggered by POSTing to the target URI of the link.
SAP-OutSystems Security protocols
B-Synergy delivers the service of a one-day SAP-OutSystems security audit. That can help the CIO responsible for SAP-OutSystems integrations decide on SAP-OutSystems measures to take, and architectures to follow.
SAP IDOC with OutSystems
IDoc, short for Intermediate Document, is an SAP document format for business transaction data transfers.[1] Non SAP systems can use IDocs as the standard interface (computing) for data transfer.[2] IDoc is similar to XML in purpose but differs in syntax. Both serve the purpose of data exchange and automation in computer systems, but IDoc-Technology takes a different approach.
While XML allows having some metadata about the document itself, an IDoc is obliged to have information at its header like its creator, creation time etc. While XML has a tag-like tree structure containing data and meta-data, IDocs use a table with the data and meta-data. IDocs also have a session that explains all the processes in which the document passed or will pass, allowing one to debug and trace the status of the document.
Different IDoc types are available to handle different types of messages. For example, the IDoc format ORDERS01 may be used for both purchase orders and order confirmations.
When this order cannot be created because of an application error (for example: The price per piece is lower than allowed for this material), then the administrator on the vendor's system sees this IDoc among the erroneous ones and can solve the situation. If the error is in the master data at the vendor's system, he can correct them and order the IDoc to be processed again.
Because of the flexibility and transparency of IDoc technology, some non-SAP technologies use them as well.